Les services oignon sont des services auxquels ont ne peut accéder que par Tor. Exécuter un service oignon donne à vos utilisateurs toute la sécurité du HTTPS avec les bénéfices supplémentaires du Navigateur Tor en termes de vie privée.
Pourquoi des services oignon ?
Les services oignon offrent divers avantages en termes de vie privée et de sécurité pour les personnes qui les utilisent.
Cacher la localisation
L’adresse IP d’un service oignon est protégée. Les services oignon sont une surcouche réseau au dessus de TCP/IP. Dans un certain sens, les adresses IP ne sont pas significatives pour les services oignon : elles ne sont même pas utilisées dans le protocole.
Authentification de bout en bout
Quand un utilisateur visite un oignon particulier, il sait que le contenu qu’il voit ne peut venir que de cet oignon particulier. Aucune usurpation d’identité n’est possible, ce qui est rarement le cas. Habituellement, atteindre un site Web ne signifie pas qu’un intercepteur n’a pas réacheminé votre connexion vers un autre emplacement (p. ex. attaques DNS).
Chiffrement de bout en bout
Le trafic des services oignon est chiffré du client jusqu’à l’hôte oignon. C’est comme obtenir un HTTPS/SSL fort gratuitement.
Traversée du NAT
Est-ce que votre réseau est filtré et vous ne pouvez pas ouvrir des ports sur votre pare-feu ? Cela peut arriver si vous êtes sur un campus universitaire, un bureau, un aéroport ou potentiellement n’importe où. Les services oignon n’ont pas besoin de port ouvert parce qu’ils traversent le NAT. Ils établissents uniquement des connections sortantes.
Le protocole de service oignon : vue d’ensemble
Maintenant la question devient quel genre de protocol est nécessaire pour atteindre toutes ces propriétés ? Habituellement les personnes se connectent à une adresse Ip et voilà, mais comment se connecter à quelque chose qui n’a pas d’adresse IP ?
En particulier, l’adresse d’un service oignon ressemble à ceci :
vww6ybal4bd7szmgncyruucpgfkqahzddi37ktceo3ah7ngmcopnpyyd.onion
Cela semble étrange et aléatoire parce que c’est la clef publique d’identification du service oignon. C’est une des raisons pour lesquelles nous pouvons atteindre les propriétés de sécurité ci-dessus.
The onion service protocol uses the Tor network so that the client can introduce itself to the service, and then set up a rendezvous point with the service over the Tor network. Voici la répartition détaillée des étapes pour y arriver :
Acte 1 : quand le service oignon met en place ses points d’introduction
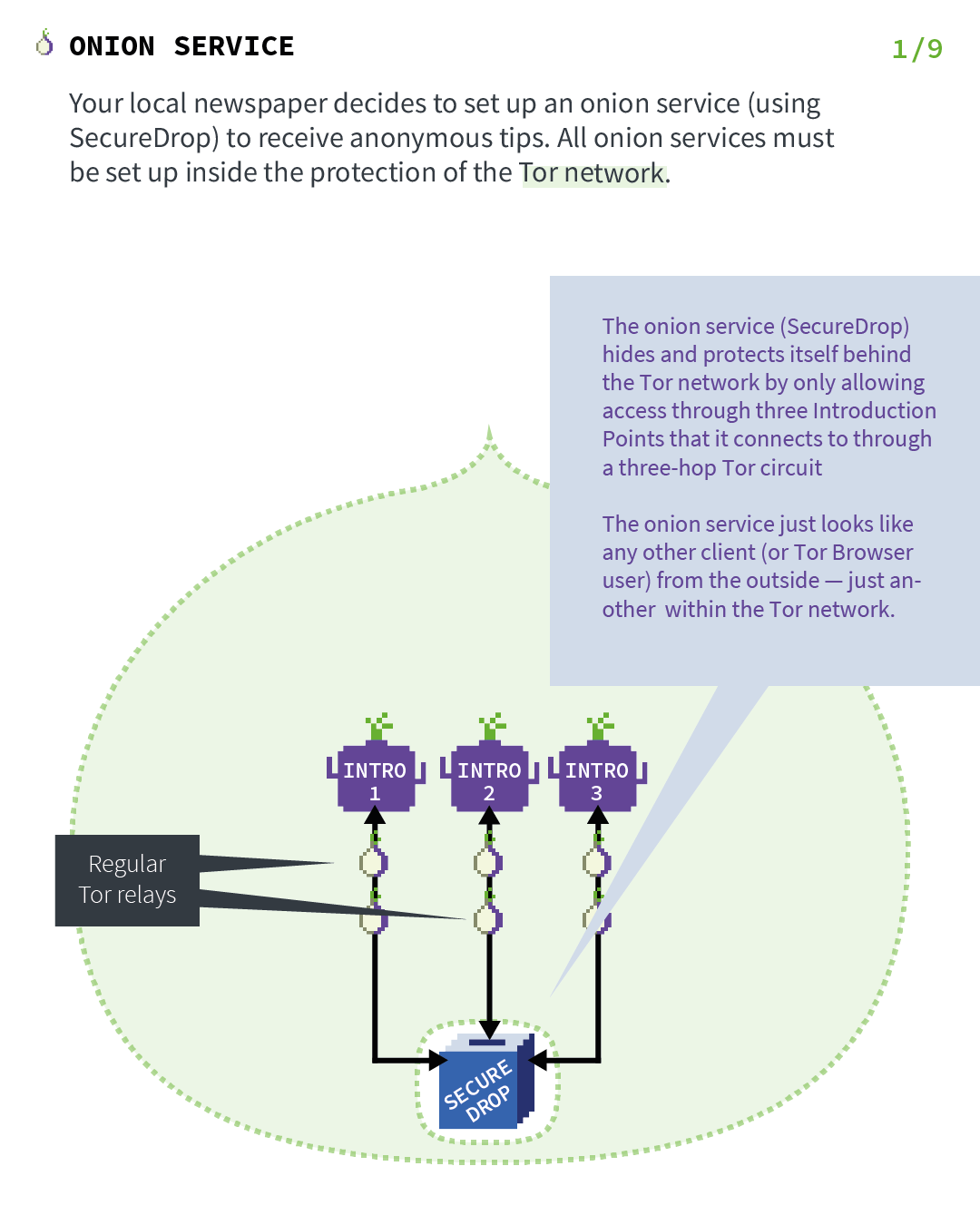
Let's imagine that your local newspaper decides to set up an onion service (using SecureDrop) to receive anonymous tips. As the first step in the protocol, the onion service will contact a bunch of Tor relays and ask them to act as its introduction points by establishing long-term circuits to them. These circuits are anonymized circuits, so the server does not reveal the service location to the introduction points.
The onion service will hide and protect itself behind the Tor network by only allowing access through three introduction points that it connects to through a two-hop Tor circuit.
Acte 2 : quand le service oignon publie ses descripteurs.
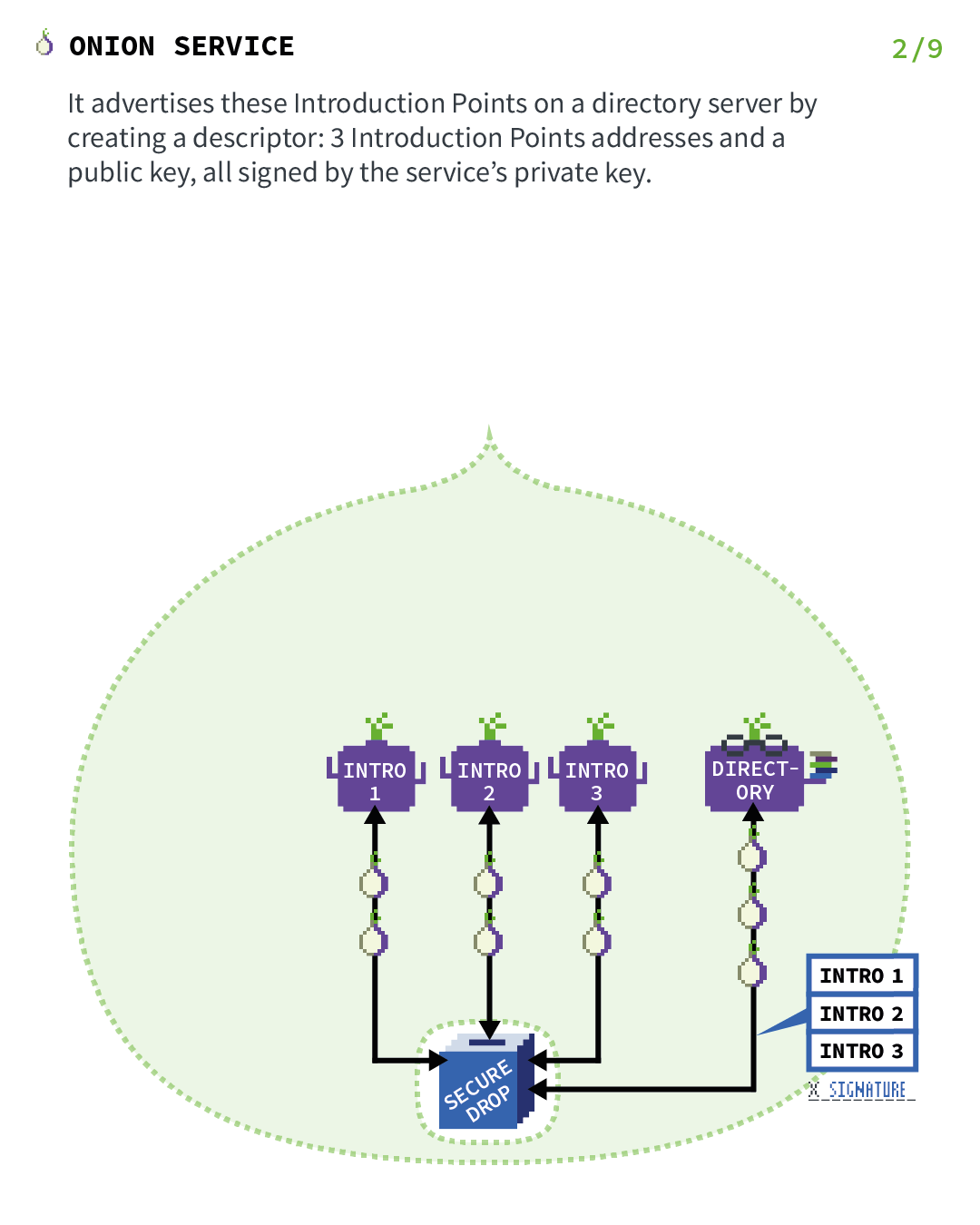
Now that the introduction points are set up, we need to create a way for clients to be able to find them.
For this reason, the onion service assembles an onion service descriptor, containing a list of its introduction points (and "authentication keys"), and signs this descriptor with the onion service's identity private key. La clef privée d’identification utilisée ici est la partie privée de la clef publique encodée dans l’adresse du service oignon.
The onion service upload that signed descriptor to a distributed hash table, which is part of the Tor network, so that clients can also get it. It uses an anonymized Tor circuit to do this upload so that it does not reveal its location.
Act 3: Where a client wants to visit the onion service
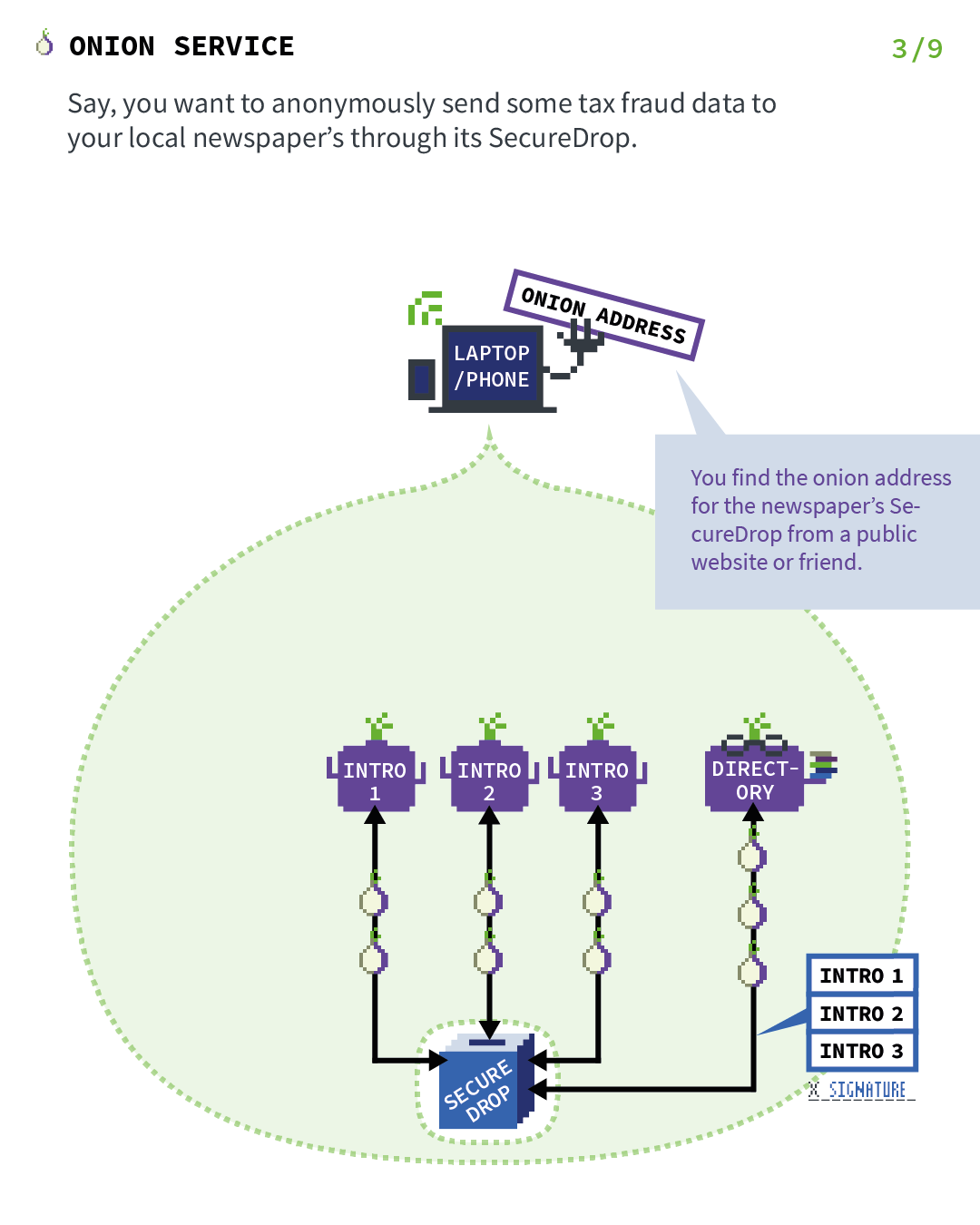
Say you want to anonymously send some tax fraud data to your local newspaper through its SecureDrop. You find the onion address for the newspaper's SecureDrop from a public website or friend.
Act 4: Where the client introduces itself to the onion service
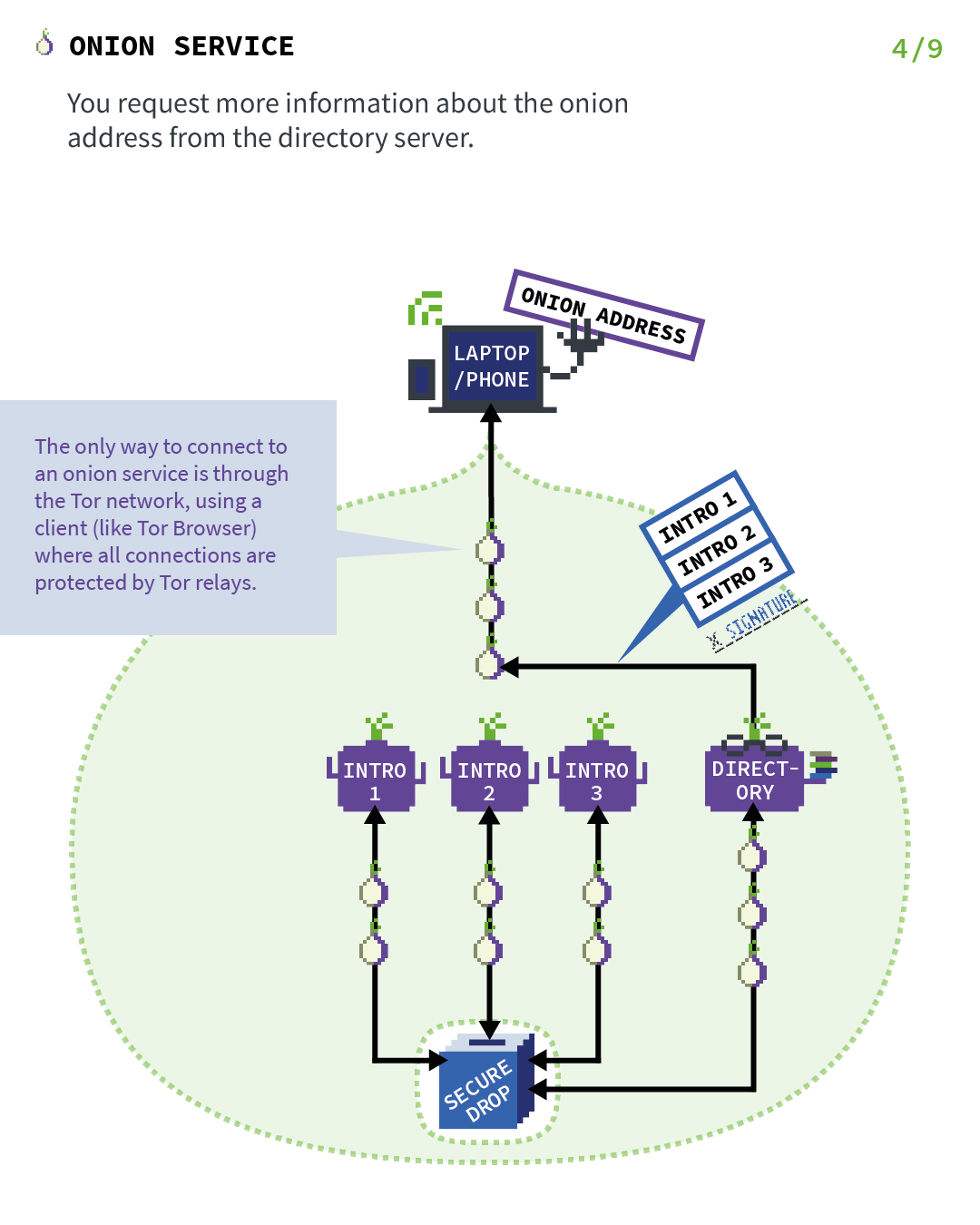
All the previous steps were just set up for the onion service so that it's reachable by clients. Now let's fast-forward to the point where an actual client wants to visit the service.
In this case, the client has the onion address of SecureDrop and want to visit it, so they connect to the service with Tor Browser. Now the next thing that needs to happen is that the client goes to the distributed hash table from Step 2 and ask for the signed descriptor of SecureDrop's onion service.
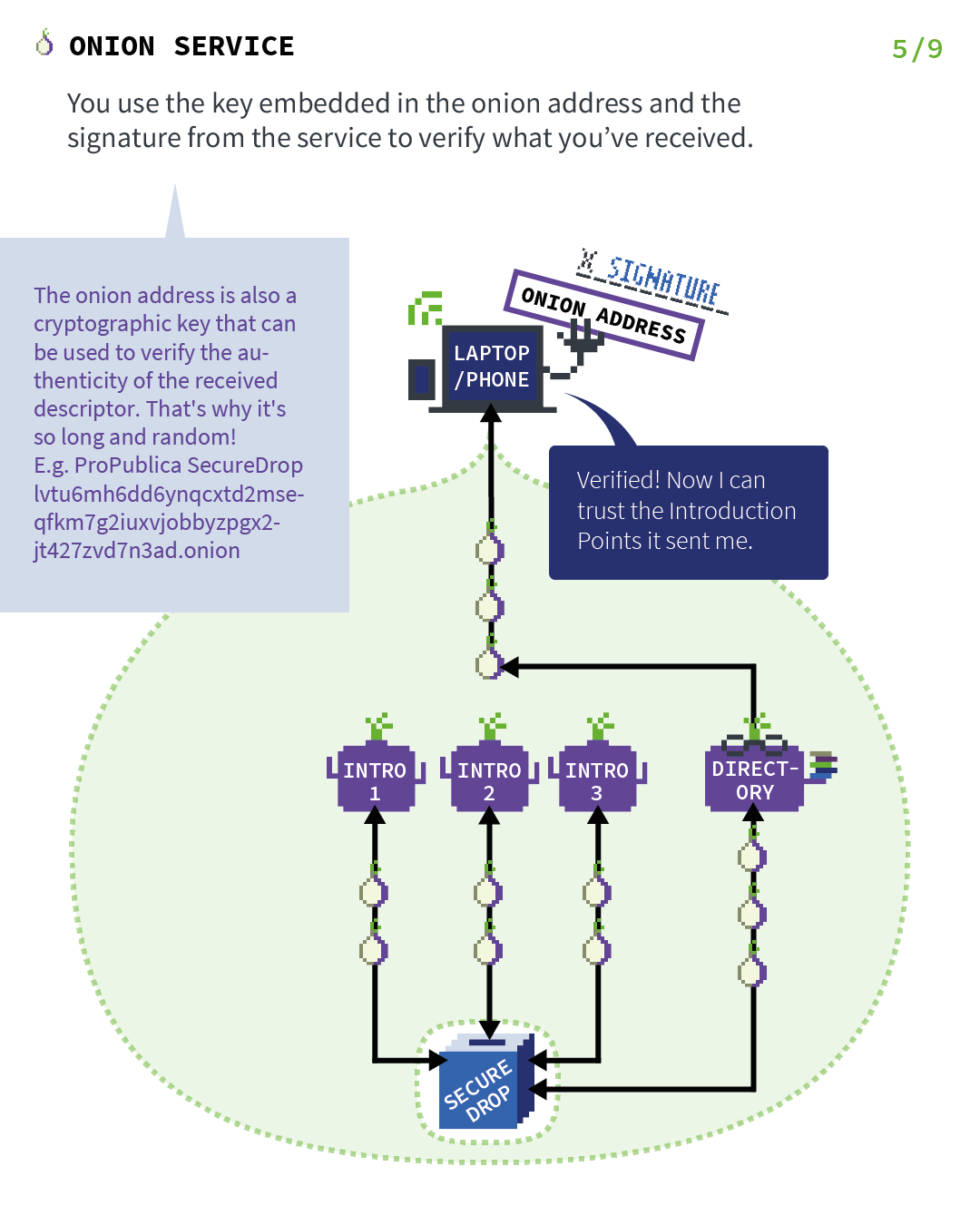
Act 5: Where the client verify onion address signature
When the client receives the signed descriptor, they verify the signature of the descriptor using the public key that is encoded in the onion address. This provides the end-to-end authentication security property, since we are now sure that this descriptor could only be produced by that onion service and no one else.
And inside the descriptor, there are the introduction points that allow the client to introduce themselves to SecureDrop's onion service.
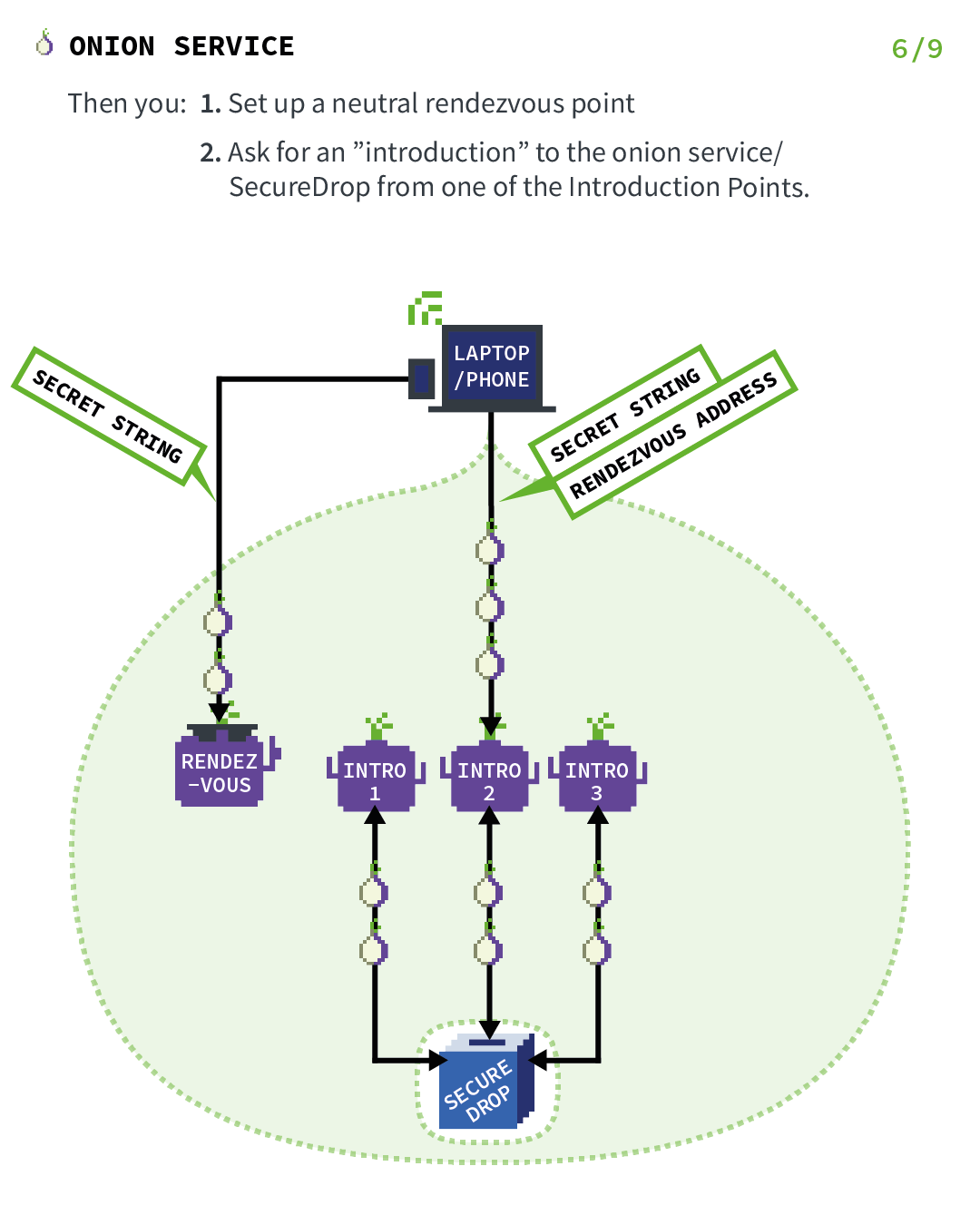
Act 6: Where the client establishes a rendezvous point
Before the introduction takes place, the client (in this case, you) picks a Tor relay and establishes a circuit to it. The client asks the relay to become their rendezvous point and give it an "one-time secret" that will be used as part of the rendezvous procedure.
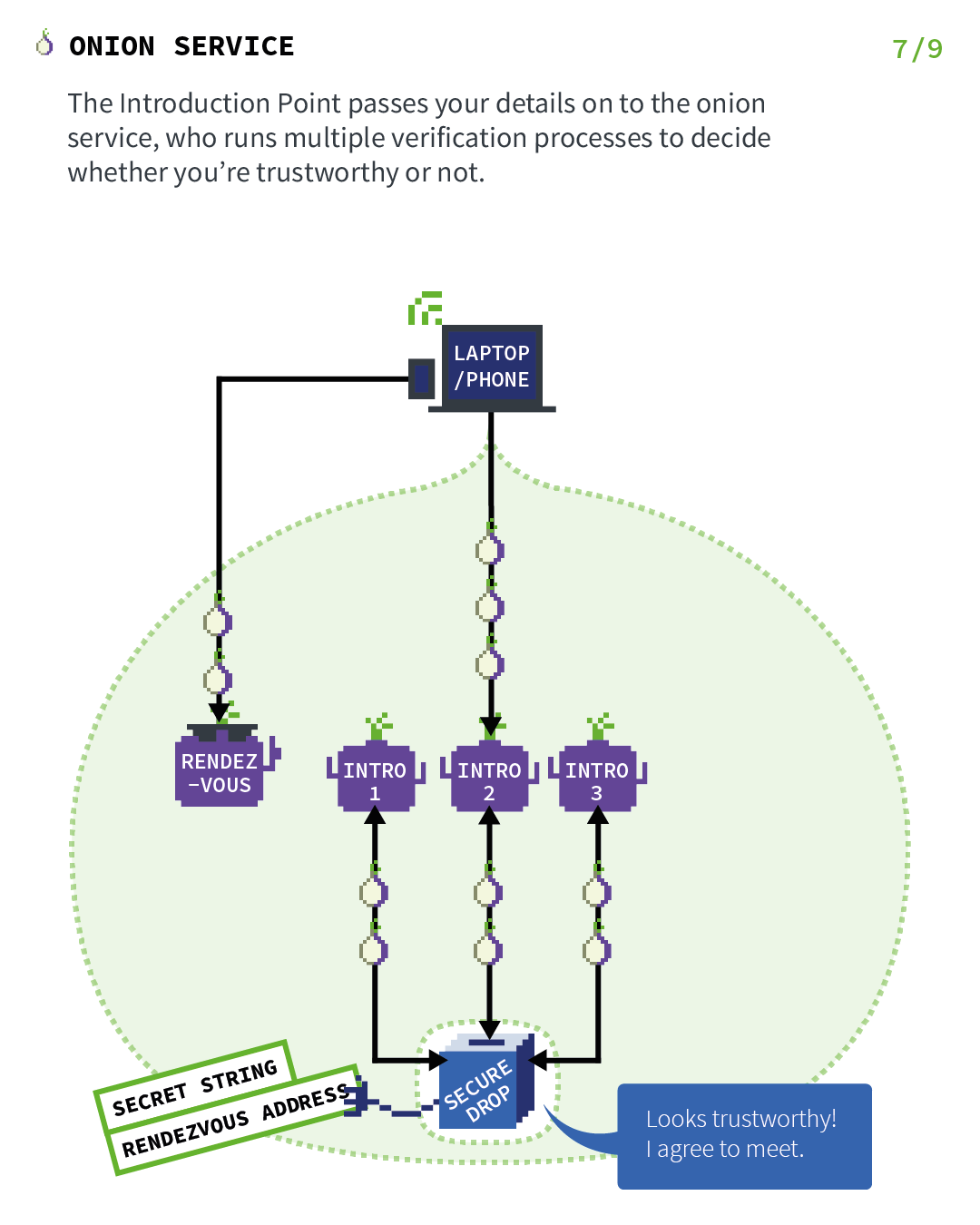
Act 7: Where the onion service rendezvous with the client
The introduction point passes your details (secret string and rendezvous address) on to the onion service, which runs multiple verification processes to decide whether you're trustworthy or not.
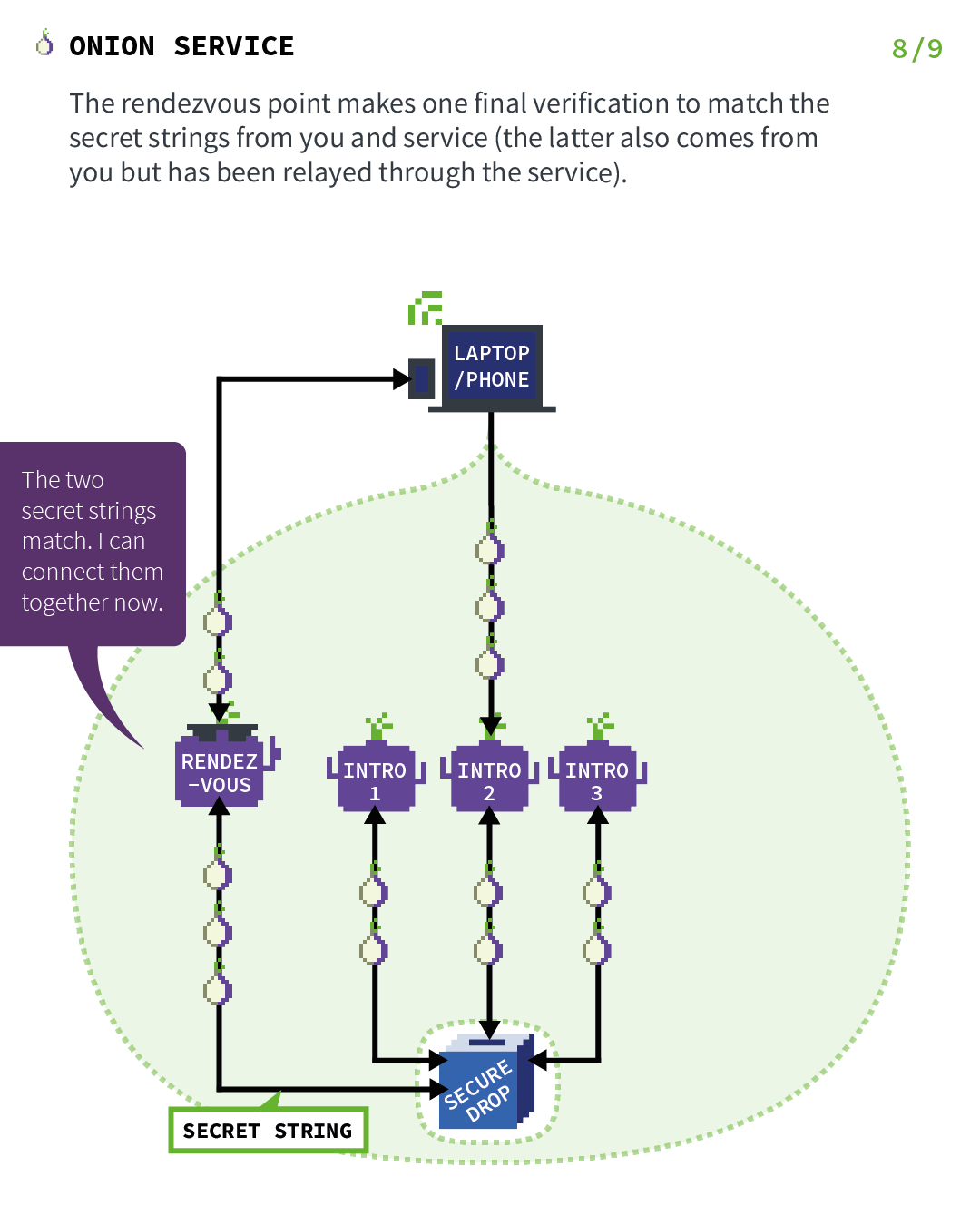
Act 8: Where the rendezvous point verifies the client's secret
Le service oignon se connecte au point de rendezvous (à travers un circuit anonymisé) et lui envoie le "secret à usage unique".
The rendezvous point makes one final verification to match the secret strings from you and service (the latter also comes from you but has been relayed through the service).
Le point de rendezvous relaie (avec chiffrement de bout en bout) les messages du client vers le service et vice versa.
Act 9: Where the onion service rendezvous with the client
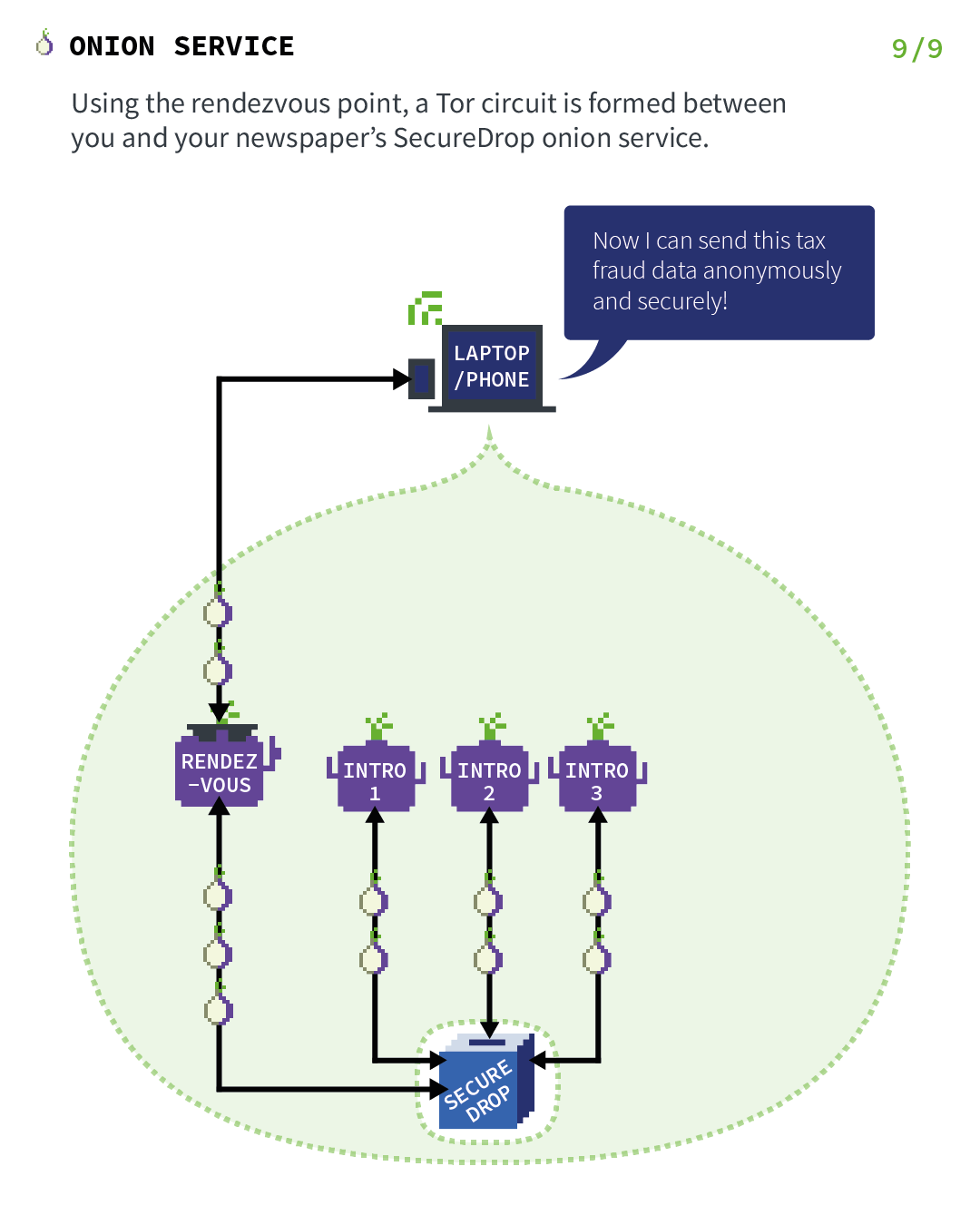
In general, the complete connection between client and onion service consists of 6 relays: 3 of them were picked by the client, with the third being the rendezvous point, and the other 3 were picked by the onion service. This provides location hiding to this connection.
Finally, using the rendezvous point, a Tor circuit is formed between you and your newspaper's SecureDrop onion service.
Autres sources d’information
Cen'était qu'un aperçu du protocole de services oignon Tor. Here are some more resources if you want to learn more:
- The Tor design paper describing the original design.
- La spécification des services oignon Tor v3 (en anglais).
- Des conférences (en anglais) à propos des services oignon : Understanding Tor Onion Services and Their Use Cases - HOPE XI 2016, DEF CON 25 - Roger Dingledine - Next Generation Tor Onion Services.
